How to configure the domain’s DNS settings?
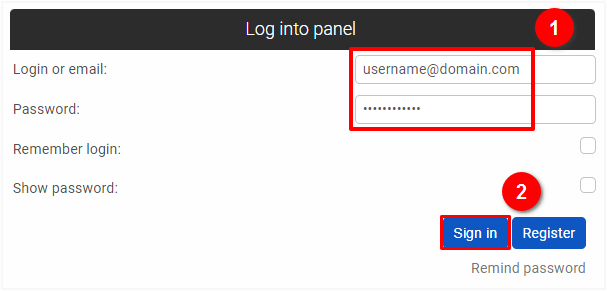
If you want to configure or edit your domain's DNS settings, go to https://CBA.pl/panel/en and enter the login details (1) i.e. the email or profile name to the user panel and the password that were set at the time of registration, and then click on the "Sign in" button (2).
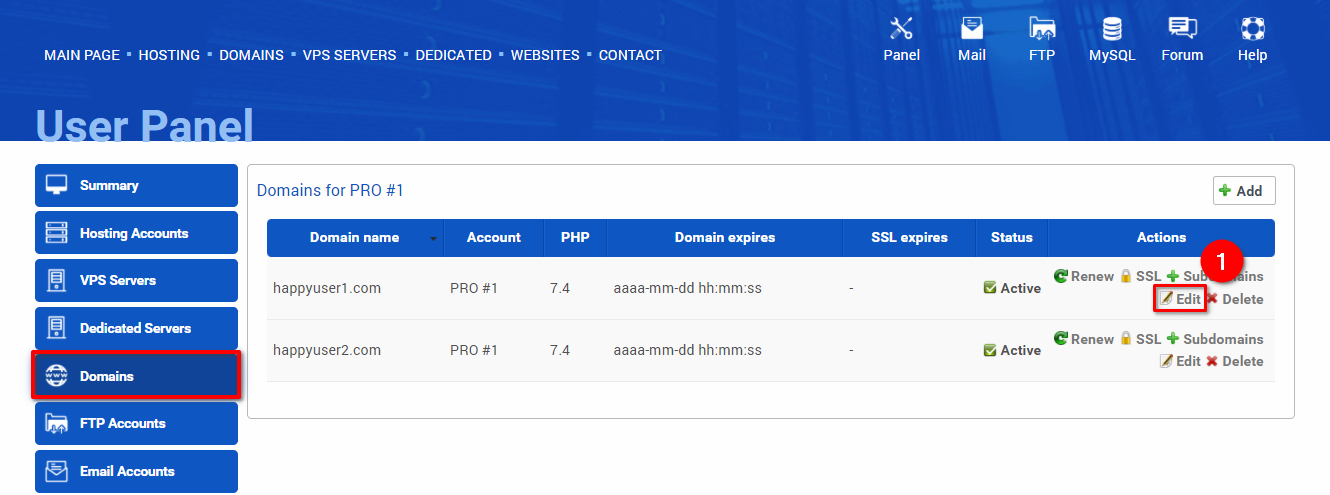
Go to the Domains section in the user panel: https://CBA.pl/panel/en/domains, and click on the “Edit” button (1) in the domain row you wish to configure.
Select the "Advanced settings" tab (1), enter the needed information, and click "Save" (2).
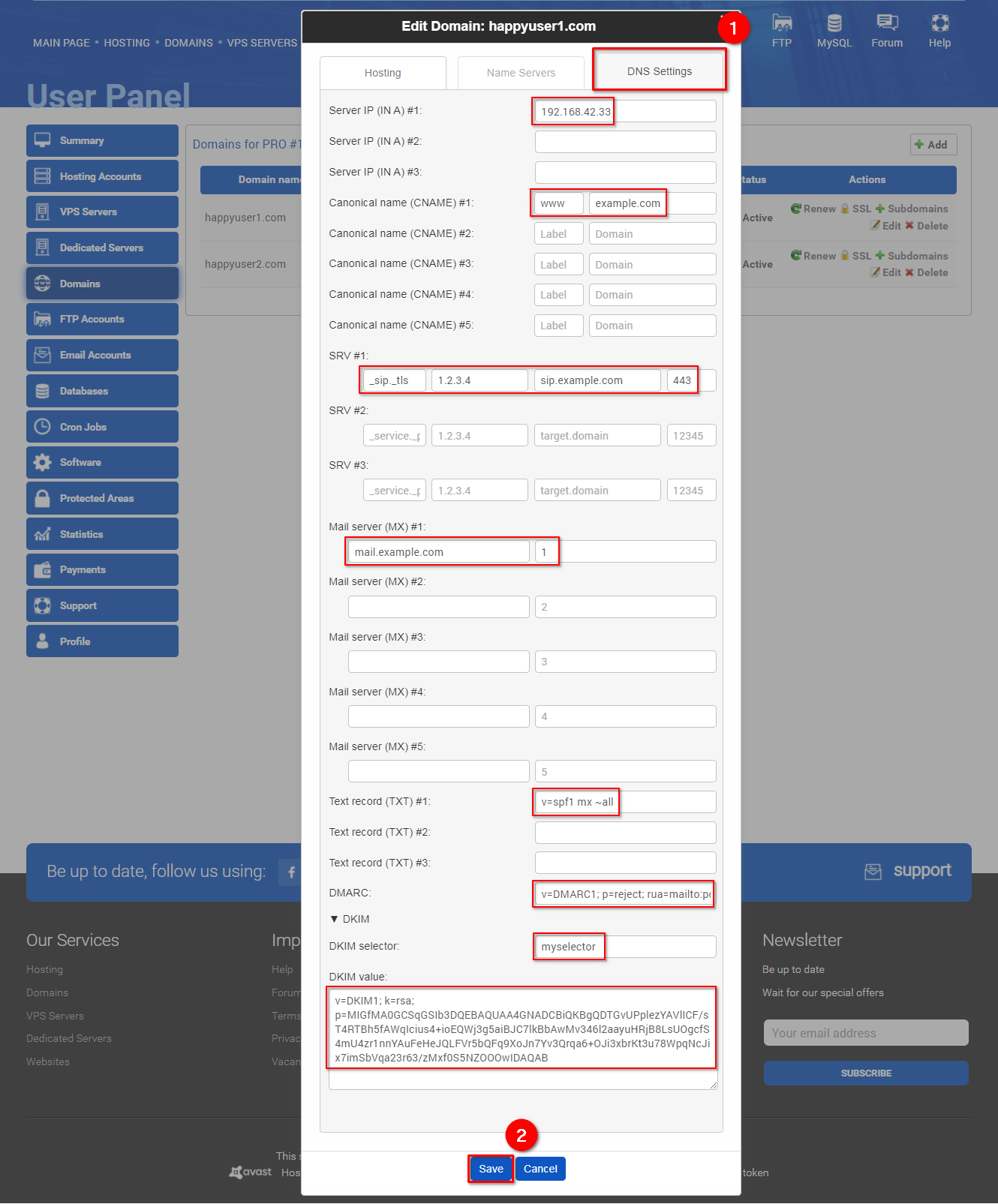
The Domain Name System settings are explained below:
- Server IP (in A): this is the most fundamental type of DNS record, it indicates the IP address of a given domain.
- Canonical name (CNAME): is a type of resource record in the DNS that maps one domain name (an alias) to another (the canonical name). This can prove convenient when running multiple services (like an FTP server and a web server, each running on different ports) from a single IP address. One can, for example, point ftp.example.com and www.example.com to the DNS entry for example.com, which in turn has an A record which points to the IP address. Then, if the IP address ever changes, one only has to record the change in one place within the network: in the DNS A record for example.com. CNAME records must always point to another domain name, never directly to an IP address.
- SRV record - a Service record is a specification of data in the Domain Name System defining the location, i.e., the hostname and port number, of servers for specified services. Some Internet protocols such as the Session Initiation Protocol (SIP) and the Extensible Messaging and Presence Protocol (XMPP) often require SRV support by network elements. Standard SRV record has format: _service._proto.name. ttl IN SRV priority weight port target.
- _service - name of the service
- _proto - transfer protocol, _tcp or _udp
- name - name of domain for which this record is valid
- ttl - time to live in DNS
- IN - DNS class field. Always IN
- SRV - type of record. Always SRV
- priority - of target host (number). Lower value means more preferred
- weight - A relative weight (number) for records with the same priority, higher value means higher chance of getting picked.
- port (number) - the TCP or UDP port on which the service is to be found.
- target - the canonical hostname of the machine providing the service
- In the first field, the concatenated _service._proto, for example, _minecraft._tcp.
- In the second field, the IP address of the target (not required).
- In the third field, the target.
- In the fourth field, the port (0-65535).
- Mail server (MX): the mail exchange (MX) record indicates how email messages should be routed in accordance with the SMTP, the standard protocol for all emails. Like CNAME records, an MX record must always point to another domain. To set up an MX record, add the domain name in the first field and its priority (0-65535) in the second field.
- Text record (TXT): text records (TXT) are multipurpose records commonly used to store contact details and general domain information. Two of its most important uses are email spam prevention and domain ownership verification.
- DMARC: the DMARC record is a DNS TXT record that contains a DMARC policy. Domain-based Message Authentication Reporting and Conformance (DMARC) is a method of authenticating email messages. Basically, DMARC tells the receiving email server to: (a) allow the message to continue delivery, reject the message or quarantine it, and (b) sends reports to an email address or addresses with data about all the messages seen from the domain. Value of this record will be visible in _dmarc.domain. For example, if your domain is example.com and you input:
v=DMARC1; p=quarantine; rua=mailto:postmaster@example.com
then record will be read as this: _dmarc.example.com. 3600 IN TXT "v=DMARC1; p=quarantine; rua=mailto:postmaster@example.com" - DKIM: The DKIM record is a DNS TXT record that contains the DKIM public key. The DomainKeys Identified Email (DKIM) is a method of email authentication that helps prevent spammers from impersonating a legitimate domain - public key (only makes sense currently for VPSes), copy appropriate fragment (it does not work flawlessly yet)
 Hosting protected by Avast software
Hosting protected by Avast software